|
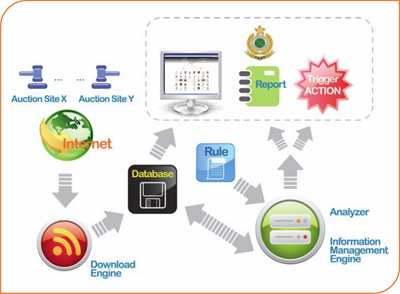
As people routinely spend more and more time at their computers, shopping online has become an increasingly popular occupation. But along with the trend has come a rise in the cases of intellectual property (IP) infringement and of the auctioning online of fake designer goods. HKU's Centre for Information Security and Cryptography (CISC), working hand in hand with the Customs and Excise Department of the HKSAR, has developed a solution to the problem with the Lineament Monitoring System II (LMS II). This new computer system makes it possible to monitor the web 24/7, an ability that previously was simply too costly in terms of manpower. Dr Chow Kam-pui, Associate Professor of the Department of Computer Science and Associate Director of the Centre for Information Security and Cryptography, explains that the system combines the latest techniques in cyber-criminal profiling, artificial intelligence (AI) and web crawling. Crawler, analysers, rules "The Lineament Monitoring System II is divided into three parts," explains Pierre Lai, recent PhD graduate of the Department and part of the team that developed the system. "First the 'Crawler', which collects data from targeted auction sites then performs a semantic analysis of the crawled information. Second the 'Analysers', which further monitor the data before it is analysed by the system's profiling and AI engines. And third, the 'Rules', which are the criteria chosen by a Customs officer – for example he/she might stipulate that the system looks out for a certain model of car being offered within a certain price range. If the specified Rules come up with respect to a certain bid, the LMS II sends an alarm email direct to the officer." Before the LMS II, monitoring of illegal auctions on the Internet was tedious, inefficient and time-consuming. Customs officers had to sit at a computer screen for hours waiting for something to happen. To make matters worse, the illegal traders had become very good at evading capture. One trick was to set up a sale, then open the bidding for just a few short hours, before agreeing a price and instantly erasing all incriminating evidence. Under the LMS II, the officers simply choose key words that they want the system to search for – such as sellers, brands and price range – and the system does the monitoring 24 hours a day and stores the resulting information. |
“New technology enables
the |
|
| Profiling ability |
Dr Chow explains that a further key feature of the LMS II is its profiling ability. "It makes analysis of different accounts, vendors and goods easy. New technology enables the LMS II to assess if the same person may be behind several accounts or transactions. This information is then forwarded to the Customs officers to investigate further." In 2010, cases of counterfeit goods being sold online rose 15 per cent on 2009, with 45 cases detected. The counterfeit goods mainly comprised accessories, watches, clothes, leather goods and sunglasses. Since its launch in January this year, the LMS II, which costs about $300,000, has been used in the investigation of more than 120 cases, of which almost 70 have been resolved. Customs officials say that most of the people involved in this kind of 'peer-to-peer' sale, are employed but on a low salary and are looking to make quick money. The LMS II marks the second collaboration between HKU's Centre for Information Security and Cryptography and Hong Kong's Customs and Excise Department. The first, back in 2005, resulted in the original Lineament Monitoring System which was developed to track copyright protected materials that are shared online, such as movies and songs. "Customs and Excise wanted to monitor BitTorrent activities, a technology which enabled anyone to download movies," says Dr Chow. "We developed the LMS to do it automatically after which Customs and Excise successfully arrested the 'Big Crook' who shared three movies using BitTorrent a few years ago. Two years ago, we invited Customs to attend our annual CISC workshop at which we present our latest research and development. Customs showed interest in our technology that monitored Internet auction activities, and started talking about the possibility of developing a system to track the auction of fake goods online – the result was the LMS II." Asked about the future of the LMS II, Dr Chow says he and his team of four full-time engineers will keep updating and improving it. "In the near future, we will also further cooperate with other Hong Kong law enforcement agencies like the police and the Immigration Department to develop new technologies to help fight cyberspace crime," he adds. |
Illicit activity on the Internet is changing constantly as people find ever more ingenious ways to sidestep the law. "Our next system will probably involve finding a way to deal with 'cyber lockers', places where data can be stored without any traceable connection to who put it there . . . for example torrent files that are used by BitTorrent," says Dr Chow. "Moreover, these lockers also allow people to stream media, rather than download it, making their actions very difficult to track. It is likely that the problem of how to deal with cyber lockers and tracing media streaming will be the basis for the Lineament Monitoring System III." |
|
| Back | Next | |